#
How Splunk Enhances All Functional Groups in the SOC
Part IV
A mature Security Operations Center (SOC) typically includes the following functional groups:
#
Continuous Monitoring for Cybersecurity
Threat Intelligence, Incident Handling, Forensics, and Self-Assessment
"Not everything that can be counted counts and not everything that counts can be counted."
— Albert Einstein, Physicist
The focus should not be on a specific data source or technology but rather on the broader concept of observability.
IT operations refer to the activities and processes involved in maintaining and managing the technology infrastructure, systems, and applications of an organization. This can include tasks such as installing and configuring hardware and software, monitoring systems and networks for issues or outages, and troubleshooting and resolving problems as they arise.
IT observability, on the other hand, refers to the ability to monitor, measure, and understand the performance and behavior of IT systems, networks, and applications. This can include collecting and analyzing data from various sources, such as log files, performance metrics, and traffic patterns, to identify trends, issues, and potential problems.
The main difference between IT operations and IT observability is that IT operations focus on the day-to-day management and maintenance of IT systems, while IT observability focuses on understanding and optimizing the performance and behavior of these systems. Both are important for ensuring the smooth and reliable operation of an organization's technology infrastructure, but they serve different purposes and use different approaches and tools.
Threat intelligence, incident handling, forensics, and self-assessment can all be important factors in a continuous monitoring approach to cybersecurity.
Threat intelligence refers to information about potential threats or vulnerabilities that an organization may face, such as new malware strains or zero-day exploits. This information can be used to inform continuous monitoring efforts by helping to identify potential risks and vulnerabilities, and to prioritize the most important areas to focus on.
Incident handling refers to the process of responding to and managing security incidents or breaches, such as malware infections or unauthorized access to sensitive data. This can be an important part of continuous monitoring because it helps to identify and address potential issues as they arise, and to prevent further damage or loss.
Forensics refers to the process of collecting, analyzing, and preserving digital evidence for the purpose of investigating security incidents or crimes. This can be an important part of continuous monitoring because it helps to identify the root causes of incidents or breaches, and to understand the extent of the damage or loss.
Self-assessment refers to the process of evaluating an organization's security posture and identifying areas for improvement. This can be an important part of continuous monitoring because it helps to identify weaknesses or vulnerabilities that may not be immediately apparent, and to take steps to address them.
Continuous monitoring with respect to cybersecurity involves continuously collecting and analyzing data from various sources, such as threat intelligence feeds, security logs, and network traffic, to identify potential risks and vulnerabilities, and to respond to and manage incidents or breaches as they arise. By using tools and processes such as threat intelligence, incident handling, forensics, and self-assessment, organizations can improve their ability to identify and mitigate potential threats, and to maintain a strong security posture.
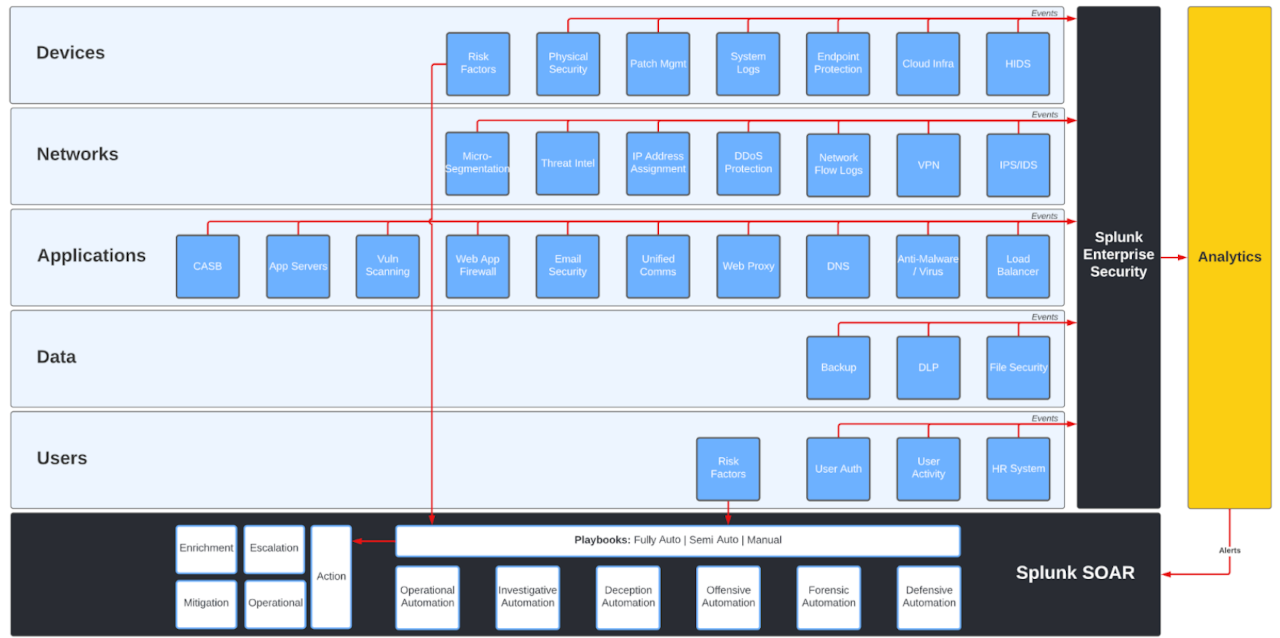
Cybersecurity Operations and Monitoring teams running a Security Operations Center (SOC) require data analytics at operational speed.
#
Benefits of Constant Introspection for IT Organizations
Constant introspection refers to the process of continuously monitoring and analyzing the performance and behavior of an organization's technology infrastructure, systems, and applications. This practice can provide numerous benefits for IT organizations, including:
Identifying potential bottlenecks or issues that may be impacting system performance.
Understanding resource requirements and planning for future capacity needs.
Identifying potential vulnerabilities or threats.
Ensuring compliance with relevant regulations and standards.
Identifying the root causes of problems and addressing them.
By implementing constant introspection, IT organizations can optimize the performance and efficiency of their systems, improve security, and ensure compliance.
#
Tracking Key Performance Indicators for IT Systems and Applications
#
Performance Monitoring
Performance monitoring and capacity planning are important activities for ensuring the smooth and reliable operation of an organization's technology infrastructure, systems, and applications. Some specific key performance indicators (KPIs) that an organization can track when it comes to these activities include:
This KPI measures the percentage of time that a system is available and functioning as expected. This can be important for ensuring that systems are meeting the needs of users and customers.
This KPI measures the time it takes for a system or application to respond to a request. This can be important for ensuring that systems are responsive and perform well.
This KPI measures the amount of data or transactions that a system or application can process in a given time period. This can be important for understanding the capacity and performance of a system.
This KPI measures the percentage of requests or transactions that result in errors. This can be important for identifying potential issues or problems with a system.
This KPI measures the percentage of available resources (such as CPU, memory, or storage) that are being used by a system or application. This can be important for understanding capacity and performance, and for identifying potential bottlenecks or issues.
This KPI measures the percentage of available capacity (such as bandwidth or storage) that is being used by a system or application. This can be important for understanding capacity and performance, and for identifying potential bottlenecks or issues.
Tracking these and other KPIs can help organizations to understand the performance and capacity of their IT systems and applications, and to identify potential issues or problems that may need to be addressed.
#
Compliance Monitoring
Compliance monitoring and root cause analysis are important activities for ensuring that an organization's technology infrastructure, systems, and applications are operating in a compliant and effective manner. Some specific key performance indicators (KPIs) that an organization can track when it comes to these activities include:
This KPI measures the percentage of transactions or processes that are compliant with relevant regulations and standards. This can be important for ensuring that an organization is meeting its compliance obligations.
This KPI measures the number of instances in which an organization's systems or processes are found to be non-compliant. This can be important for understanding the extent to which an organization is meeting its compliance obligations.
This KPI measures the time it takes for an organization to bring its systems or processes into compliance after a violation has been identified. This can be important for ensuring that issues are addressed promptly and effectively.
This KPI measures the financial cost of maintaining compliance with relevant regulations and standards. This can be important for understanding the resources that are required to meet compliance obligations.
This KPI measures the percentage of problems or issues that are successfully addressed at the root cause level. This can be important for ensuring that issues are not just being patched over, but are being fully resolved.
This KPI measures the average time it takes to resolve a problem or issue. This can be important for understanding the efficiency and effectiveness of an organization's problem-solving processes.
This KPI measures the average time between failures or issues with a system or application. This can be important for understanding the reliability and stability of a system.
This KPI measures the average time it takes to detect a problem or issue. This can be important for identifying and addressing problems as soon as possible.
Tracking these and other KPIs can help organizations to understand the compliance and reliability of their IT systems and applications, and to identify and address potential issues or problems that may need to be addressed.
#
Incident Response
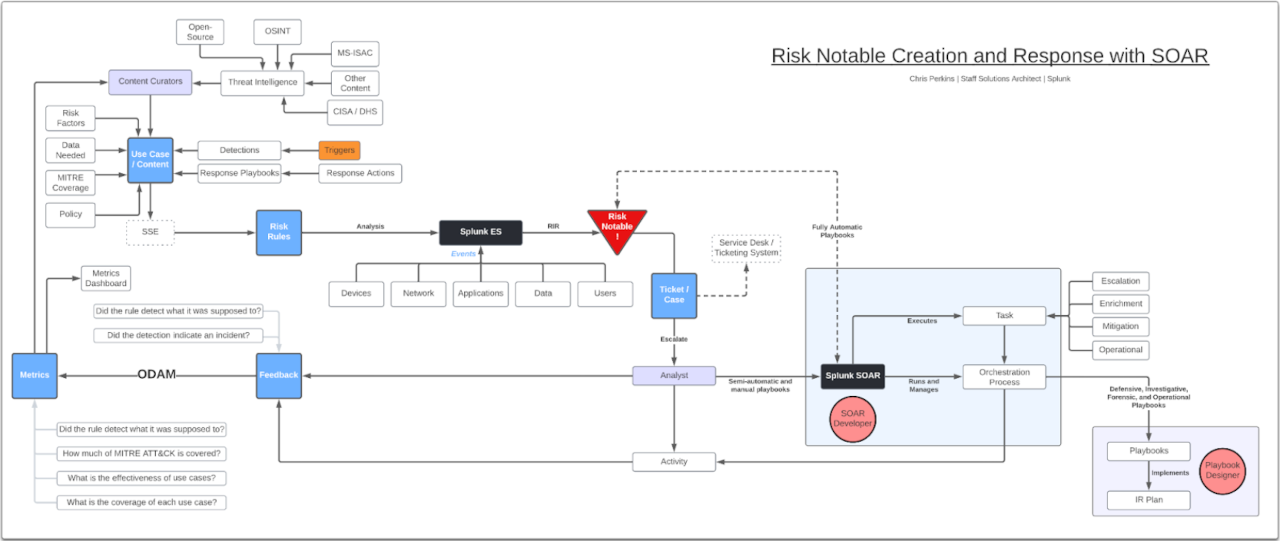
Incident response is the process of managing and responding to security incidents or other disruptions that may impact an organization's technology infrastructure, systems, or applications. Some specific key performance indicators (KPIs) that an organization can track when it comes to incident response include:
This KPI measures the average time it takes to identify a security incident or other disruption. This can be important for identifying and addressing issues as soon as possible.
This KPI measures the average time it takes to respond to a security incident or other disruption. This can be important for ensuring that issues are addressed promptly and effectively.
This KPI measures the average time it takes to recover from a security incident or other disruption. This can be important for ensuring that systems are restored and operational as quickly as possible.
This KPI measures the total number of security incidents or disruptions that an organization experiences over a given time period. This can be important for understanding the frequency and impact of such incidents.
This KPI measures the severity or impact of security incidents or disruptions on an organization. This can be important for understanding the potential impact of such incidents and for prioritizing response efforts.
Tracking these and other KPIs can help organizations to understand the effectiveness of their incident response processes, and to identify areas where improvements may be needed.